 |
Scott Jordan | |
|
|
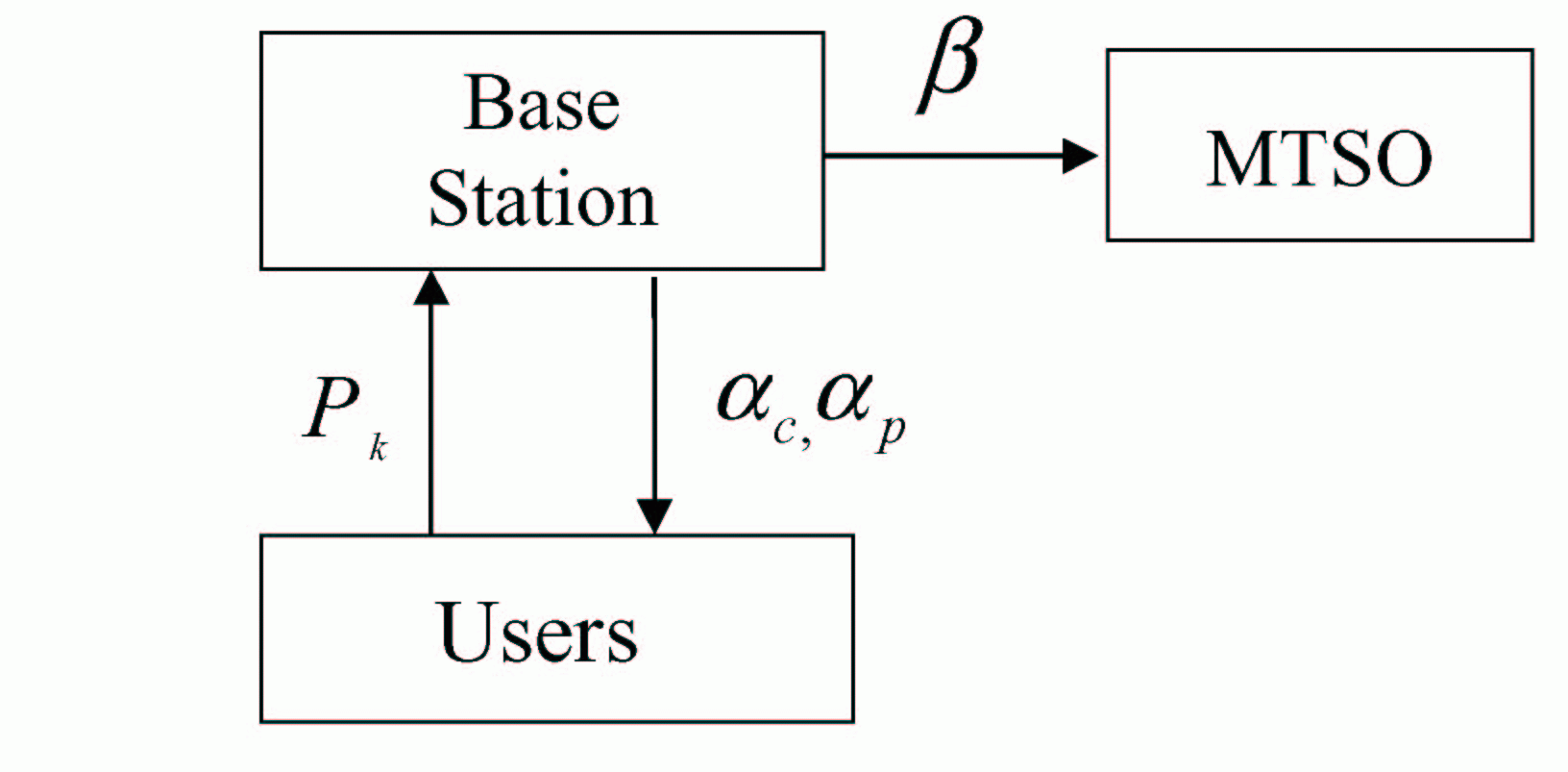 Our focus in this work is on dynamic pricing of network resources for cellular networks. The work is characterized by four aspects:
Our focus in this work is on dynamic pricing of network resources for cellular networks. The work is characterized by four aspects:
- Pricing is dynamic, on a time scale that is slower than fast power control but quicker than connection access control.
- Resources are allocated to users in a fashion that maximizes social welfare or service provider revenue.
- Prices are used to signal the relationship between the wireless channel and the resources required to obtain desired QoS.
- Users are assumed to be cooperative, not game-playing. Cooperation may be induced through charges to users.
Our goal is use pricing to dynamically allocate radio resources (power, codes, and/or data rate) to competing users to optimize an overall network objective criterion while satisfying Quality of Service constraints. We explicitly consider the effect of load-based interference between neighboring cells..
The first paper presents some of the earliest work in the field of wireless pricing. We consider here only voice service in a single cell, and show how pricing of power and codes can be used to dynamically allocate resources in a distributed fashion.
Single-Cell Forward Link Power Allocation Using Pricing in Wireless Networks (with P. Liu, P. Zhang, M.L. Honig), IEEE Transactions on Wireless Communications, vol. 3 no. 2, March 2004, pp. 533-543.
The second set of papers explicitly considers the effect of neighboring cells upon each other. We characterize when coordination is required between the two cells to achieve the system-wide optimum allocation, and how this coordination can be achieved through exchange of a price per unit power representing the externality.
Two-Cell Power Allocation for Downlink CDMA (with C. Zhou, P. Zhang, M.L. Honig), IEEE Transactions on Wireless Communications, vol. 3 no. 6, November 2004, pp. 2256-2266.
Forward-Link Resource Allocation for a Two-Cell Voice Networks with Multiple Service Classes (with C. Zhou, M.L. Honig, R. Berry), IEEE Wireless Communications and Networking Conference, New Orleans, Louisiana, March 2003, pp. 1060-1065.
The third set of papers considers data rather than voice service. Data applications are assumed to have utility that increases concavely with SINR. Prices are associated with power in each cell. We prove that if the power budget is low, then no coordination is required between neighboring cells. However, if the power budget is high, then not only is coordination required, but it can not be accomplished through exchange of an externality price.
Utility-Based Power Control for a Two-Cell CDMA Data Network (with C. Zhou, M.L. Honig), IEEE Transactions on Wireless Communications, vol. 4 no. 6, November 2005, pp. 2764-2776.
Utility-Based Resource Allocation for Wireless Networks with Mixed Voice and Data Services (with C. Zhou, M.L. Honig, R. Berry), IEEE International Conference on Computer Communications and Networks, Miami, Florida, October 2002, pp. 485-488.
Dynamic Resource Allocation for Integrated Voice and Data Traffic in DS-CDMA (with J.B. Kim, M.L. Honig), IEEE Vehicular Technology Conference, Atlantic City, New Jersey, October 2001, pp. 42-46.
The next paper considers the effect of dynamic arrivals and departures of data users upon allocation of power. Utility is associated with the time required for file transfer. Pricing is used to allocate power to competing data streams.
Packet-Based Power Allocation for Forward Link Data Traffic (with P. Liu, R. Berry, and M. Honig), IEEE Transactions on Wireless Communications, vol. 6 no. 8, August 2007, pp. 2894-2903.
The next set of papers consider applications which are in between the extremes of inelastic real-time and elastic best-effort. Here, we attempt to provide QoS to such interactive applications. In the first paper, interactive users can specify a target througput to be achieved over the duration of the connection. We propose a packet scheduler that balances efficiency with fairness by combining a max-min policy with a policy of serving users with relatively good channels. In the second paper, interactive users can specify both a minimum throughput and a maximum rate variance. We characterize the power and rate control policy that minimizes the peak total transmit power. In the third paper, users can specify thresholds on short term throughputs. We present algorithms that maximize the probability of satisfying these thresholds.
Cross Layer Dynamic Resource Allocation with Targeted Throughput for WCDMA Data (with P. Zhang), IEEE Transactions on Wireless Communications, vol. 7 no. 12, December 2008, pp. 4896-4906.
Downlink Power Control with Throughput and Rate Variation Guarantees (with N. Chen), IEEE Wireless Communications and Networking Conference (WCNC), Hong Kong, China, March 2007, pp. 3430-3435.
Downlink Scheduling with Guarantees on the Probability of Short-term Throughput (with N. Chen), IEEE Transactions on Wireless Communications, vol. 8 no. 2, February 2009, pp. 593-598.
The next set of papers continues the focus on applications which are in between the extremes of inelastic real-time and elastic best-effort. However, unlike the papers above, these applications are now explicitly modeled using sigmoid (s-shaped) utility functions. Whereas elastic applications only require rate scheduling, we find that semi-elastic applications require both rate scheduling and connection access control. The first paper considers the case in which utility is a semi-elastic function of the rate achieved in each time slot. We propose a near-optimal algorithm that iteratively finds optimal shadow prices for power and rates. The second paper considers the case in which utility is a sigmoid function of the average bit rate over multiple time slots. We are particularly motivated here by video conferencing. We show that greedy allocation to maximize incremental utility in the current time slot can be implemented in a distributed fashion by an exchange of price and demand amongst users, the network, and an intermediate power allocation module. We then propose resource allocation that considers both the average rate achieved so far and the future expected rate, and show how future expected rate can be estimated by modeling the probability that a user will be allocated a subcarrier in a future time slot.
Downlink User Selection and Resource Allocation for Semi-Elastic Flows in an OFDM Cell (with C. Yang), ACM Journal of Wireless Networks, vol. 19 no. 6, August 2013, pp. 1407-1421.
Power and Rate Allocation for Video Conferencing in Cellular Networks (with C.Yang), EURASIP Journal on Wireless Communications and Networking, February 2013, 2013:31.
Resource Allocation for Semi-elastic Applications with Outage Constraints in Cellular Networks (with C. Yang), IEEE Transactions on Vehicular Technology, vol. 64 no. 4, April 2015, pp. 1591-1606.
A Novel Coordinated Connection Access Control and Resource Allocation Framework for 4G Wireless Networks (wth C. Yang), IEEE/ACM Transactions on Networking, vol. 23 no. 4, August 2015, pp. 1328-1341.
Portions of this work were supported by DARPA and NSF. Any opinions, findings, conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Science Foundation, DARPA, or IEEE. This material is presented to ensure timely dissemination of scholarly and technical work. Copyright and all rights therein are retained by authors or by other copyright holders. All persons copying this information are expected to adhere to the terms and constraints invoked by each author's copyright. One print or electronic copy may be made for personal use only. Permission must be obtained from the copyright holder for systematic or multiple reproduction, distribution to multiple locations via electronic or other means, duplication of any material in these papers for a fee or for commercial purposes, modification of the content of these papers, reprinting or republishing of this material for advertising or promotional purposes or for creating new collective works for resale or redistribution to servers or lists, and to reuse any copyrighted component of this work in other works.